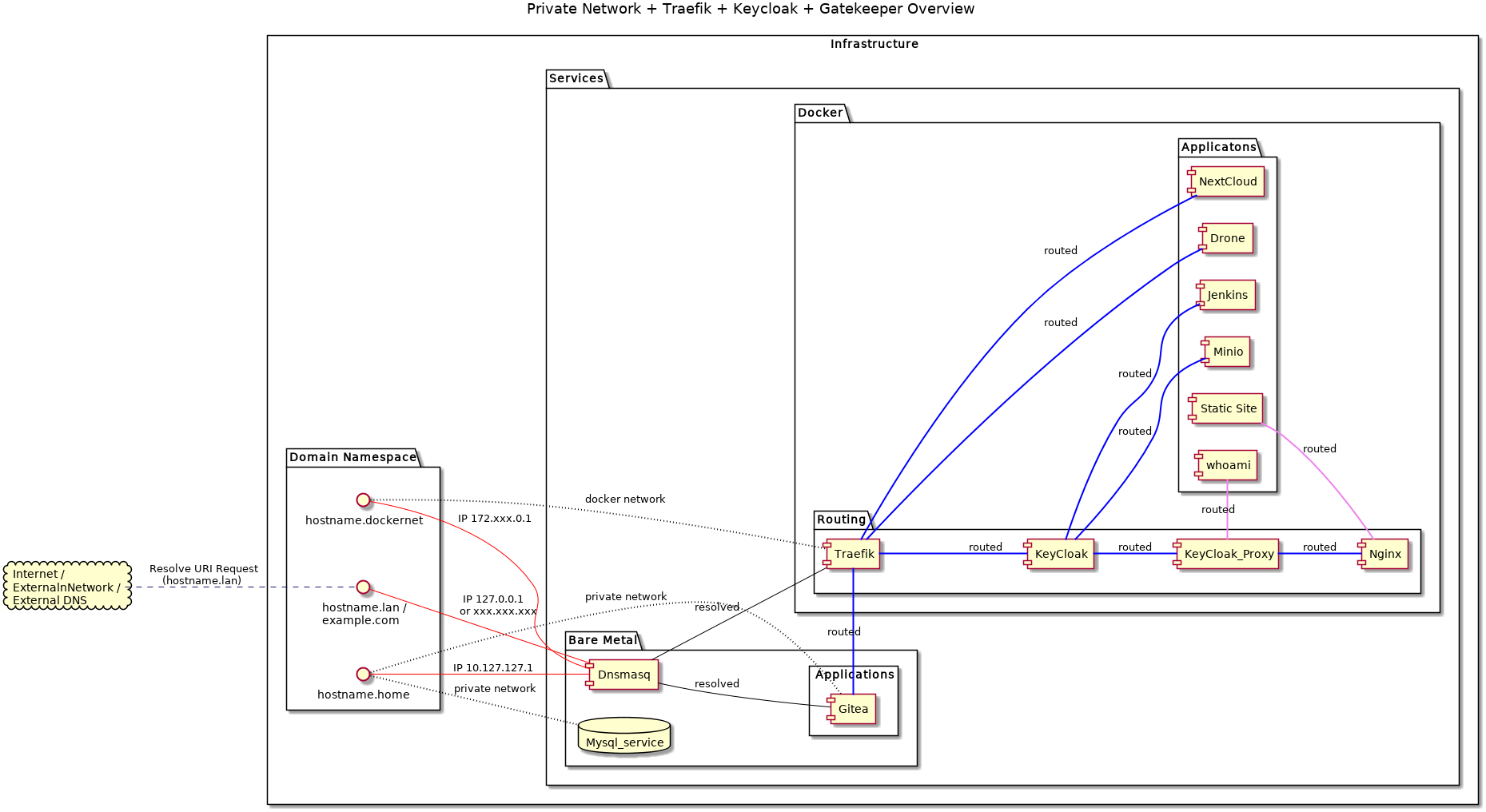
Private Network + Traefik + Keycloak + Gatekeeper Overview (diagram)
A high level network overview of Traefik, Keycloak, and Gatekeeper working together
This is yet another artifact [although ugly] from a project I’m working on. This diagram depicts a basic lab infrastructure with Traefik, Keyclaok, and Keycloak Gatekeeper working together behind a local DNS (dnsmasq). Details for how all of this actually fits together are forthcomming. For now, hopefully, it will be helpful for those who are wondering what the layout looks like when configuring these various components to work together.