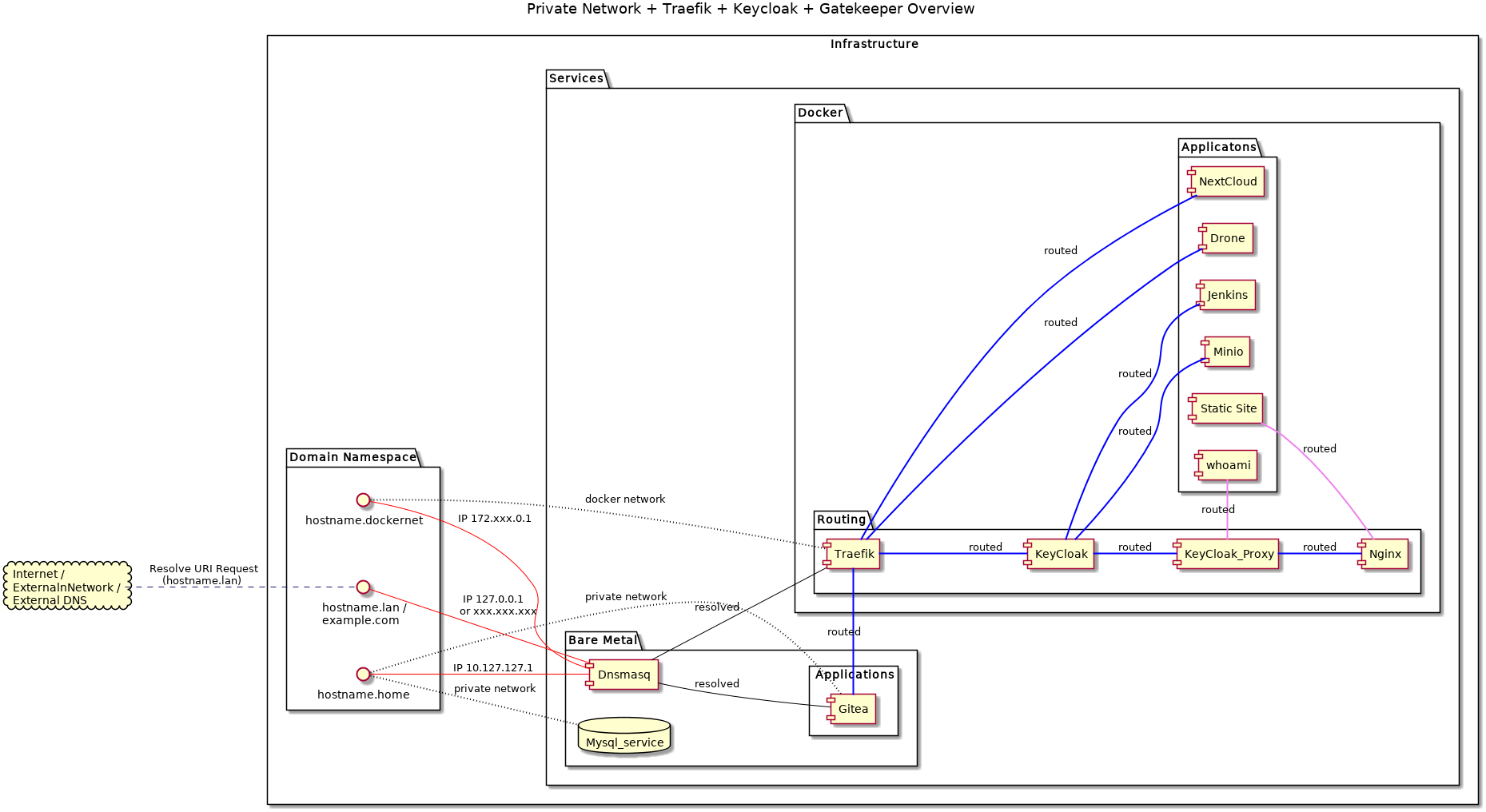
Keycloak v5 + Gatekeeper v5: Flowcharts - Easily Create and Restrict an Isolated (IODC) Client Service by Group-Role
This is another artifact from an upcoming series of articles that I’m writing for creating a home/laptop development laboratory ecosystem. I’m sharing these artifacts now because the series that I’m writing won’t be released for at least a month (It’s a huge undertaking -for me).
These flow charts demonstrate the simplest form (IMHO) of creating Keycloak client services behind an authentication/authorization proxy (Keycloak Gatekeeper). I imagine that if you are reading this article you are already frustrated with just creating a simple client in Keycloak and/or trying to figure out how to restrict authorization so that only specific users of a group are allowed to log in via Keycloak.